Authenticate to S3 using an EC2 IAM Role
With the release of SQL Backup Master v6.1.586.0, you can now authenticate your Amazon S3 backups directly via an IAM role assigned to an EC2 instance. This approach eliminates the need to store or input S3 credentials in SQL Backup Master—helping to streamline security and simplify setup.
Instead of entering your access key and secret key, SQL Backup Master will automatically use the EC2 IAM role to access your S3 bucket(s). Below is a quick guide on configuring both your EC2 environment and SQL Backup Master.
CONFIGURING THE EC2 ENVIRONMENT
1. Create an IAM role within the AWS IAM console. 2. Attach the AmazonS3FullAccess permission (or a policy granting the necessary S3 access) to this IAM role. 3. Assign the new role to the EC2 instance where SQL Backup Master is installed.
For detailed steps on creating and attaching IAM roles to EC2 instances, refer to the official AWS documentation: https://docs.aws.amazon.com/IAM/latest/UserGuide/id_roles_use_switch-role-ec2.html
CONFIGURING SQL BACKUP MASTER
1. Install or upgrade to SQL Backup Master v6.1.586.0 (or later) on the EC2 instance. 2. Open or create a database backup job that uses Amazon S3 as the destination. 3. Select Authenticate using EC2 IAM role instead of entering an access key and secret key. Leave those fields blank.
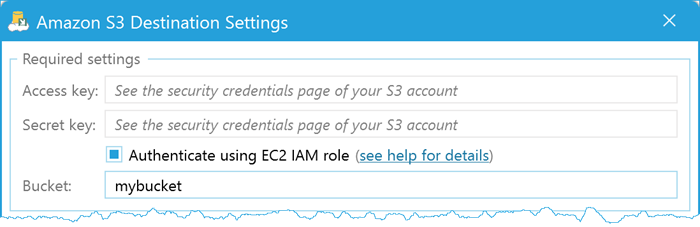
Finally, run your backup job to ensure everything is working correctly. SQL Backup Master will automatically leverage your EC2 IAM role for the necessary permissions to upload backups to S3.
That’s it! By using an EC2 IAM role, you streamline your S3 backup process while adhering to AWS security best practices—eliminating the need to store or rotate AWS credentials within SQL Backup Master.
